Passwords! Billions of them-potentially yours-have been stolen in a massive data breach.
This isn’t just a minor inconvenience; a data breach, as defined by Kaspersky, is the unauthorized viewing and/or sharing of confidential information Kaspersky, exposing individuals and organizations to significant risks including identity theft, financial loss, and reputational damage Wikipedia. This breach, involving sophisticated “info-stealers” employing methods like malware and phishing, will be examined in detail, revealing its scale, impact, and the crucial steps individuals and organizations must take to enhance their cybersecurity defenses and prevent future attacks. This blog post will cover the scale of this alarming breach, explain how it happened, and outline practical steps to protect yourself and your organization.
The Billions of Exposed Credentials
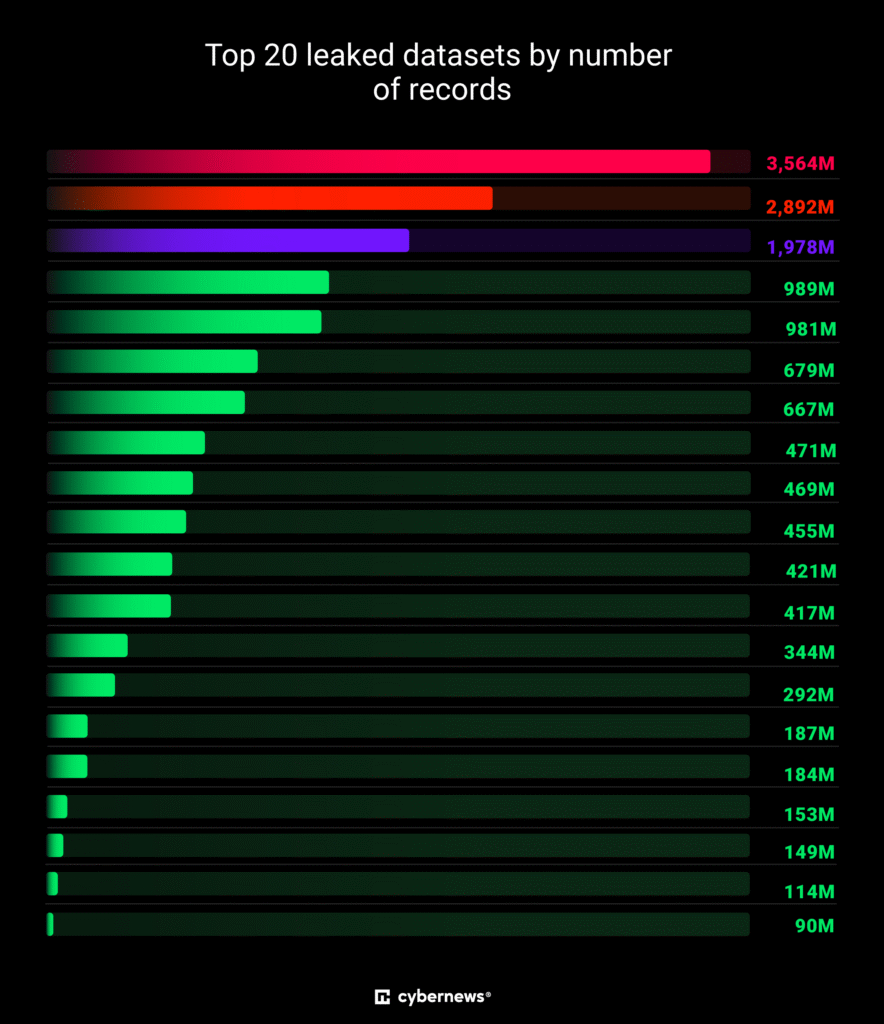
Imagine a world where billions of digital identities secured with your passwords are suddenly vulnerable, exposed to the malicious intent of cybercriminals. This isn’t a fictional scenario; it’s the stark reality of a recent massive data breach. The sheer scale of this incident is unprecedented, impacting countless individuals and organizations globally. A data breach, as defined by experts, is a security incident where unauthorized individuals gain access to sensitive information IBM, Crowdstrike. This can encompass personal data like Social Security numbers and bank account details, as well as corporate information such as customer records and intellectual property. The consequences are severe, ranging from identity theft and financial losses to reputational damage for businesses.
Central to this breach are info-stealers, sophisticated cybercriminals who employ various methods to infiltrate systems and steal data. Their techniques often involve malicious software, cleverly crafted phishing scams, and exploiting vulnerabilities within software or networks. Read how this recent massive data breach mainly exposing passwords, examining its magnitude, consequences, root causes, and ultimately, what individuals and organizations can do to better safeguard themselves. Understanding the methods of these info-stealers is crucial in developing effective prevention strategies.
This alarming situation demands immediate attention and proactive measures. The widespread exposure of billions of passwords and credentials necessitates a comprehensive understanding of the breach’s scope and impact. The Data Breach: Scale, Impact, and Methods
The sheer scale of the recent data breach is staggering; billions of credentials have been compromised, representing a significant threat to individuals and organizations alike. This unprecedented event underscores the critical need for robust cybersecurity measures. A data breach, as defined by numerous sources, involves unauthorized access to sensitive information, resulting in potentially devastating consequences PCMAG, Redbotsecurity, Breachsense. The compromised data likely includes a variety of sensitive information such as usernames, passwords, email addresses, and potentially even financial details, depending on the targeted systems. The impact extends far beyond simple inconvenience.
For individuals, the consequences can be severe, potentially leading to identity theft and financial loss. Imagine the scenario: someone uses your stolen credentials to open fraudulent accounts in your name, resulting in significant debt and a lengthy process to restore your credit rating. Reputational damage can also be considerable, particularly given the potential for the misuse of personal information that can lead to long-term harm. Organizations, on the other hand, face substantial financial losses stemming from legal fees and regulatory fines. Beyond this, reputational damage can seriously affect a company’s future business prospects, causing significant financial instability and trust erosion among clients and partners.
The methods employed by info-stealers are sophisticated and often involve a combination of techniques. Malware, such as keyloggers, can secretly record user inputs, providing criminals with access to credentials without the victim ever knowing. Phishing campaigns, designed to trick users into revealing their login details, remain a surprisingly effective tactic. Furthermore, the exploitation of software vulnerabilities, often unknown to the system administrators, allows nefarious actors to gain unauthorized access to systems containing a wealth of sensitive data. The success of these attacks highlights that a comprehensive approach covering strong password practices combined with updated software is critical for prevention. Understanding the vulnerabilities is equally, perhaps more, important.
While precise statistics on the affected parties and data types remain unavailable at this time, a comprehensive investigation will likely reveal a much wider range of damages impacting many more groups than initially reported. The sheer number of credentials compromised suggests a widespread impact, affecting not just individuals but also larger companies and other organizations. Further inquiry will shed light on many of these aspects. Prevention and Mitigation Protecting Yourself
Approach to Safegaurd
Safeguarding yourself and your organization from the devastating effects of data breaches requires a proactive approach encompassing individual responsibility and robust organizational security measures. For individuals, implementing strong passwords is paramount; avoid easily guessable combinations and utilize a password manager to securely store complex and unique credentials for each account. Multi-factor authentication, adding an extra layer of security beyond just a password, significantly reduces the risk of unauthorized access, even if your password is compromised. Regularly updating your software and applications is crucial, patching vulnerabilities that malicious actors could exploit. Staying vigilant against phishing emails and other social engineering tactics is essential; suspicious links or unexpected requests for personal information should always be treated with extreme caution and verified through official channels. Careful consideration of the websites and applications you use can also mitigate your exposure to vulnerabilities. Prioritize reputable services with a proven history of secure practices. Simple measures like these collectively improve your online safety.
What Should an Organization Do?
Organizations must implement comprehensive cybersecurity strategies extending beyond individual user habits. Providing comprehensive employee security training significantly enhances workforce awareness of phishing scams and other threats, preparing them to identify and react appropriately. Regular security audits, performed both internally and externally by qualified professionals, allow for the identification and remediation of existing vulnerabilities before they can be exploited. Employing data encryption safeguards sensitive information, even if a breach occurs, protecting data from unauthorized access. A robust incident response plan, outlining preemptive measures, detection, recovery, and communication protocols, is vital for minimizing the damage and recovery time associated with a security incident. By strengthening these layers of organizational defense, organizations effectively decrease the likelihood of successful attacks and lessen their impact. The combination of individual vigilance and robust organizational policies forms a powerful defense against the ever-evolving threat of data breaches.
The sheer scale of this data breach underscores the critical need for robust cybersecurity practices. While the specifics of how this breach occurred remain under investigation, the impact is undeniable. The billions of compromised credentials highlight the urgent necessity for strong, unique passwords for every online account, coupled with multi-factor authentication where available. Regularly updating passwords and utilizing password managers can significantly mitigate the risk of future compromises. Stay vigilant, and prioritize your online security. (reviewtechs)
FAQ’s
Q1: What exactly happened in this data breach?
A1: A massive security breach exposed approximately 16 billion credentials, potentially giving hackers access to accounts across major platforms including Facebook, Google, and Apple through stolen login information.
Q2: How could this breach affect me personally?
A2: If your credentials were compromised, attackers could access your accounts, leading to identity theft, financial fraud, or unauthorized purchases using your saved payment methods.
Q3: What are “info-stealers” mentioned in the breach?
A3: Info-stealers are sophisticated malware programs that secretly harvest login credentials through methods like keylogging, phishing scams, or exploiting software vulnerabilities.
Q4: What types of information were exposed?
A4: The breach likely exposed usernames, passwords, email addresses, and potentially financial details depending on which accounts and services were compromised.
Q5: How can I check if my accounts were affected?
A5: Use reputable breach-checking tools like Have I Been Pwned or your password manager’s breach alert feature to see if your email or passwords appear in known breach databases.
Q6: What immediate steps should I take to protect myself?
A6: Immediately change passwords for critical accounts, enable multi-factor authentication everywhere possible, and monitor accounts for suspicious activity.
Q7: How can organizations protect against such breaches?
A7: Companies should implement regular security audits, employee cybersecurity training, data encryption, and have an incident response plan ready for potential breaches.
Q8: Why are password managers recommended?
A8: Password managers generate and store strong, unique passwords for each account, preventing credential reuse that could lead to multiple account compromises from a single breach.
Q9: What’s the risk if I reuse passwords across sites?
A9: Reused passwords mean if one account is breached, hackers can access all accounts using that same password – a technique called “credential stuffing.”
Q10: Where can I learn more about protecting my digital identity?
A10: Reputable sources like CISA (Cybersecurity & Infrastructure Security Agency), National Cyber Security Centre, or Kaspersky’s security blogs offer updated protection guidelines.

